Blog
Explore the latest insights, news, and research in proactive threat defense and security optimization with Tuskira.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

Vulnerability
Lessons from the 2026 CTEM Study: Crossing the Divide from Visibility to Proof
Lessons from the 2026 CTEM Study: Crossing the Divide from Visibility to Proof

Defense
The Amnesia Problem in AI SOCs: What Learning Actually Means
The Amnesia Problem in AI SOCs: What Learning Actually Means

Vulnerability
CTEM isn’t VM: Moneyballing Breach Prevention
CTEM isn’t VM: Moneyballing Breach Prevention
.png)
Defense
The Future SOC Understands Behavior
The Future SOC Understands Behavior

Vulnerability
Detecting and Responding to MongoBleed (CVE-2025-14847) with Tuskira
Detecting and Responding to MongoBleed (CVE-2025-14847) with Tuskira
Defense
The Real AI Guardrail Is Reversibility
The Real AI Guardrail Is Reversibility

Defense
Accountability for Autonomous AI Actions Is Boring, but It’s the Whole Game
Accountability for Autonomous AI Actions Is Boring, but It’s the Whole Game
Defense
Crawl, Walk, Run: The Only Safe Path to Autonomous AI
Crawl, Walk, Run: The Only Safe Path to Autonomous AI

Vulnerability
When Machines Started Talking Back: A Story About AI Security
When Machines Started Talking Back: A Story About AI Security

Defense
The Moment AI Walked Into the SOC
The Moment AI Walked Into the SOC

Remediation
Where the SOC Has Been, Where GigaOm Says It's Going
Where the SOC Has Been, Where GigaOm Says It's Going
.png)
Defense
Tuskira Launches AI Security Council for Security Leaders
Tuskira Launches AI Security Council for Security Leaders
Defense
The Real Test for AI in Security Operations
The Real Test for AI in Security Operations
Defense
Agentic AI Doesn’t Need Perfect Data
Agentic AI Doesn’t Need Perfect Data
Vulnerability
Why Orchestration Beats More Tools (and More Noise)
Why Orchestration Beats More Tools (and More Noise)

Tool Sprawl
Are We Safer? Why Agentic Orchestration Is the Answer
Are We Safer? Why Agentic Orchestration Is the Answer
Vulnerability
Does Your Vuln Score Tell You Where Attacks Will Hit?
Does Your Vuln Score Tell You Where Attacks Will Hit?
Defense
Preemptive Exposure Management, a Story by Gartner
Preemptive Exposure Management, a Story by Gartner

Defense
Are Attackers Already Using AI Against Your SOC?
Are Attackers Already Using AI Against Your SOC?

Defense
Tuskira Recognized in Gartner’s Report on Intelligent Simulation for Threat Defense
Tuskira Recognized in Gartner’s Report on Intelligent Simulation for Threat Defense

Defense
Tuskira in Gartner's Preemptive Exposure Management Report
Tuskira in Gartner's Preemptive Exposure Management Report
Defense
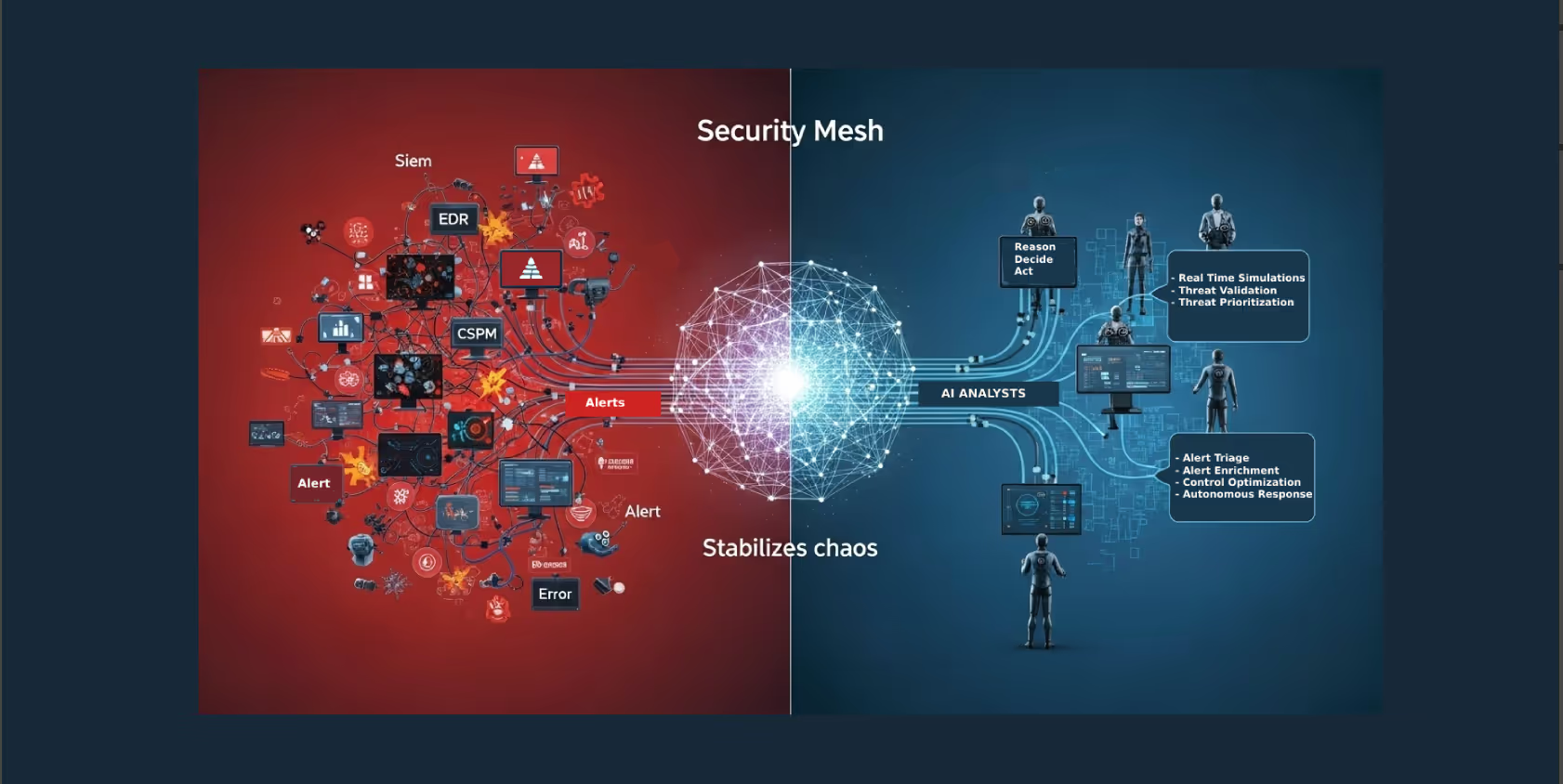
Tuskira in the Cybersecurity Mesh Architecture 3.0 Gartner Report
Tuskira in the Cybersecurity Mesh Architecture 3.0 Gartner Report

Defense
From Playbooks to Intelligence in Your SOC
From Playbooks to Intelligence in Your SOC

Tool Sprawl
Food for Thought: Turning Security Data into a Smarter Diet for AI
Food for Thought: Turning Security Data into a Smarter Diet for AI

Defense
Tuskira Announces Integration with ServiceNow to Deliver Validated, Risk-Based Security Response
Tuskira Announces Integration with ServiceNow to Deliver Validated, Risk-Based Security Response

Defense
AI Agents in Cybersecurity: The Industry is Further Along Than You May Think
AI Agents in Cybersecurity: The Industry is Further Along Than You May Think

Defense
Tuskira and Accorian Join Forces to Redefine Exposure Management for Modern Enterprises
Tuskira and Accorian Join Forces to Redefine Exposure Management for Modern Enterprises
Defense
The Immune System Was the First SOC
The Immune System Was the First SOC
Defense
What Happened When a CISO Hired AI into His Team?
What Happened When a CISO Hired AI into His Team?
Defense
Tuskira Launches Virtual AI Analysts Workforce at RSAC 2025 to Combat the Rise of AI-Based Attacks
Tuskira Launches Virtual AI Analysts Workforce at RSAC 2025 to Combat the Rise of AI-Based Attacks

Vulnerability
A CISO, a SOC Analyst, and an App Owner Walk Into a Risk…
A CISO, a SOC Analyst, and an App Owner Walk Into a Risk…

Tool Sprawl
Tool Consolidation and ROI: Are Your Security Tools Pulling Their Weight?
Tool Consolidation and ROI: Are Your Security Tools Pulling Their Weight?

Tool Sprawl
A New Way to Think About Security ROI
A New Way to Think About Security ROI
Tool Sprawl
The Debate Between Platform Bloat and Tool Sprawl
The Debate Between Platform Bloat and Tool Sprawl

Defense
March Madness: Static Defenses Lose, Adaptability Wins
March Madness: Static Defenses Lose, Adaptability Wins

Vulnerability
Rapid Exploitation Alert: Critical Apache Tomcat RCE Vulnerability (CVE-2025-24813)
Rapid Exploitation Alert: Critical Apache Tomcat RCE Vulnerability (CVE-2025-24813)

Vulnerability
AI-Driven Cyber Threats Are Escalating: Here’s What’s Changing
AI-Driven Cyber Threats Are Escalating: Here’s What’s Changing

Defense
Beyond Data Aggregation: the Power of a Security Mesh
Beyond Data Aggregation: the Power of a Security Mesh

Defense
What is a Digital Twin in Cybersecurity? (And Why Your Defenses Need One)
What is a Digital Twin in Cybersecurity? (And Why Your Defenses Need One)

Defense
Beyond Patching to Defense Validation
Beyond Patching to Defense Validation

Defense
Validating Cyber Reslience
Validating Cyber Reslience

Vulnerability
“Zero Day” on Netflix May Be Fiction, But Zero Days Are Inevitable
“Zero Day” on Netflix May Be Fiction, But Zero Days Are Inevitable

Defense
Managing Threat Exposures? Now Let AI Prove Your Defenses Work
Managing Threat Exposures? Now Let AI Prove Your Defenses Work

Vulnerability
Cutting Through 206K Vulnerabilities With Just 5 Policy Changes
Cutting Through 206K Vulnerabilities With Just 5 Policy Changes

Vulnerability
Your Security Stack is a Mess, And CTEM Alone Won’t Save It
Your Security Stack is a Mess, And CTEM Alone Won’t Save It
Defense
Breaking Down the 2025 Cybersecurity Executive Order
Breaking Down the 2025 Cybersecurity Executive Order

Defense
The SEC’s New Cyber Accountability
The SEC’s New Cyber Accountability

Vulnerability
The Silent Crisis in Vulnerability Management
The Silent Crisis in Vulnerability Management

Defense
Battling Cyberattacks in 2025: Defense Evasion and the Need for Proactive Security
Battling Cyberattacks in 2025: Defense Evasion and the Need for Proactive Security

Tool Sprawl
Are Your Cybersecurity Tools Secure?
Are Your Cybersecurity Tools Secure?

Vulnerability
Vulnerability Prioritization in 2025: Turning Noise into Actionable Insights
Vulnerability Prioritization in 2025: Turning Noise into Actionable Insights

Defense
Is ASPM Dead? Why Application Security Needs a Rethink
Is ASPM Dead? Why Application Security Needs a Rethink

Vulnerability
Why CTEM Needs a Mindset Shift
Why CTEM Needs a Mindset Shift

Defense
What Genghis Khan Can Teach Us About Modern Cyber Defense
What Genghis Khan Can Teach Us About Modern Cyber Defense

Defense
Security Data Meshes: The Key to Unified, Cost-Effective Threat Management
Security Data Meshes: The Key to Unified, Cost-Effective Threat Management

Defense
From Chaos to Harmony: How Tuskira is Preempting Cyber Defense
From Chaos to Harmony: How Tuskira is Preempting Cyber Defense

Defense
Tuskira Launches AI-Powered Unified Threat Defense Platform
Tuskira Launches AI-Powered Unified Threat Defense Platform

Vulnerability
Fix the Vulnerability or Protect Against the Exploit?
Fix the Vulnerability or Protect Against the Exploit?

Vulnerability
Why Traditional Vulnerability Management is Failing: The Need for Continuous, Behavior-Based Analysis
Why Traditional Vulnerability Management is Failing: The Need for Continuous, Behavior-Based Analysis

Tool Sprawl
The Growing Challenge of Security Tool Sprawl: How to Consolidate and Optimize Your Cybersecurity Strategy
The Growing Challenge of Security Tool Sprawl: How to Consolidate and Optimize Your Cybersecurity Strategy

Remediation
Understanding the Exploitation Window: How AI Can Narrow the Gap Between Detection and Remediation
Understanding the Exploitation Window: How AI Can Narrow the Gap Between Detection and Remediation

Defense
The Patching Problem in Cybersecurity: Why Preemptive Defense Must Be the New Standard
The Patching Problem in Cybersecurity: Why Preemptive Defense Must Be the New Standard