The Immune System Was the First SOC
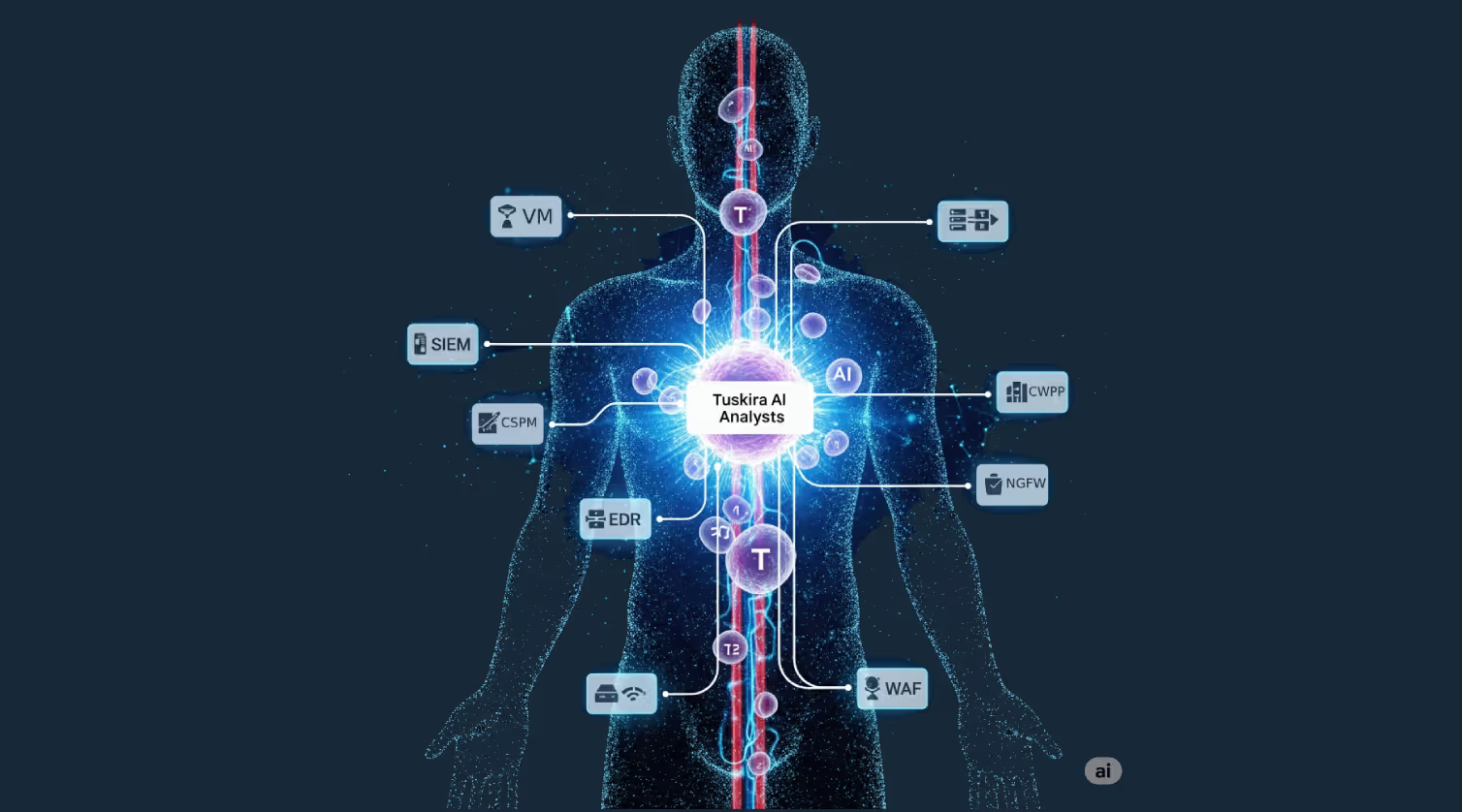
Your company is an organism. Complex. Dynamic. Growing and evolving. And just like the human body, it relies on an immune system to defend the organism. That immune system is the security ecosystem you built, consisting of an intricate network of defenses trained to identify and eliminate threats before they cause lasting harm.
However, threats evolve faster than your defenses can adapt. And just like with the human body, when the immune system can’t coordinate or keep up, viruses slip through.
A Brief Map of the Human Immune System
- Innate Defenses: Your skin, mucous membranes, and stomach acid are like firewalls and basic endpoint protections. Always on, but not adaptive.
- Natural Killer Cells (NK Cells): These are part of your innate immune system, but unlike passive barriers, they actively seek and destroy compromised cells without prior exposure. They’re fast, broad-spectrum, and can act on instinct. They’re like your WAFs and agentless tools in that they’re quick to deploy and good at spotting known behavioral patterns, but they lack deep context or the ability to adapt when the threat gets subtle.
- Macrophages & Dendritic Cells: The first responders. They recognize invaders and send out alerts like your SIEM and IDS systems, signaling that an event has occurred.
- Helper T Cells (CD4+): The coordinators. They communicate with B cells and killer T cells, determining how to fight an infection. These are the equivalent of a well-informed analyst orchestrating your response strategy.
- Cytotoxic T Cells (CD8+): The execution layer. They identify and destroy infected cells, similar to your EDRs and SOAR playbooks, though they operate with slower reaction times and without autonomous coordination.
- Memory T Cells: The immune system’s long-term memory. These cells retain knowledge of past infections and trigger a rapid response if the same pathogen returns. Similar to AI Analysts that continuously learn from prior simulations, analyst feedback, and environment changes, so the next time a similar threat appears, your system already knows how to respond. No repeat scrambling. No déjà vu triage.
- B Cells: Produce antibodies, not unlike policy rules and automated signatures for known threats.
- Suppressor T Cells: An important nuance as they prevent the immune system from overreacting. Think of them as alert suppression and prioritization logic.
But just like in biology, these systems don’t always coordinate perfectly. Some signals are over-amplified (false positives), others go unnoticed (false negatives), and attackers, like viruses, have learned how to bypass detection entirely.
Some malware behaves like a virus cloaked in a protein shell that avoids detection. Some exploits act like HIV, undermining the very defenses meant to stop them. Others trigger suppressor mechanisms, like overused alert fatigue, that reduce your team's ability to respond quickly, or at all.
In the human body, T cells are a crucial bridge. They don’t just detect, they coordinate, validate, and attack. Cytotoxic T cells destroy infected cells. Helper T cells tell other immune cells how to respond. Memory T cells ensure you don’t get fooled by the same threat twice.
That’s what Tuskira is to the cyber immune system you’ve created.
Your AI-Powered T Cell Response
Tuskira is like a system of AI-powered T-cells designed to:
- Ingest and Normalize Security Telemetry
From 150+ tools, like translating every immune signal into a common language. - Build a Real-Time Digital Twin
A living model of your environment: assets, vulnerabilities, defenses, like a body map that helps identify where infections can actually spread.
Simulate Real-World Attacks
Continuously to see what’s actually exploitable, not just flagged. Similar to how your immune system learns from past infections and tests cellular responses. - Deploy Role-Specific AI Analysts
Just like CD4+ and CD8+ T Cells, each AI Analyst specializes:
- Zero Day Analyst: Detects and simulates novel threats.
- Vulnerability Analyst: Prioritizes toxic risk based on reachability.
- Alert Analyst: Validates real threats and suppresses false positives.
- Defense Optimization Analyst: Tunes your tools like killer T Cells and calibrates immune response.
- GRC Analyst: Maps risk to compliance, ensuring audit-ready immune memory.
- AI Agents for Integration + Coordination
Immune cells coordinate using chemical messengers called cytokines, triggering actions, amplifying responses, and ensuring the immune system reacts as a unified whole. Tuskira’s integration agents play a similar role. They act as the cytokines of your security ecosystem: standardizing, syncing, and enriching telemetry across your stack so every tool receives the right context at the right time. Once a category like CSPM, EDR, or SIEM is modeled, Tuskira can autonomously generate new connectors to new tools, coordinating them to fight infections.
It’s how Tuskira scales like a living system: adaptable, intelligent, and always ready to generate the next defense layer based on your environment’s changing needs.
A Learning, Coordinated, Adaptive Immune System
With Tuskira in place:
- Your tools stop working in silos and start acting like a cohesive system.
- Your team responds faster, because the noise is filtered and the risks are validated.
- Your defenses become proactive, able to learn from attacks before they happen.
- Your posture evolves continuously, like an immune system with memory.
Your Immune System, Supercharged
- 95% False Positive Reduction
Your immune system stops chasing shadows. - 80% Reduction in Manual Triage
Tuskira filters the immune signals so your team focuses on real threats. - 60% Reduction in Exploitable Risk
Because, like real T Cells, we validate detections and act.
You’re Not Just Alerting Anymore
Tuskira works to enhance your organization’s cyber immune system. Our AI Analysts behave like helper and killer T cells, our memory layer ensures rapid response to recurring threats, NK logic eliminates broad-pattern risks fast, and our integration agents act like adaptive immune cells, generating new capabilities based on need.
Together, they turn your fragmented tools into a unified defense organism.
The human immune system has evolved to understand, remember, and act. Let’s help your security system do the same.


