The Future SOC Understands Behavior
.png)
For decades, threat hunting was a discipline practiced by people who actually knew their environment. Hunters didn’t wait for alerts. They built baselines, tracked subtle shifts in behavior, and stitched together sequences that never produced a single signature.
That fundamental hasn’t changed, but everything around it has.
Modern environments have exploded into cloud, SaaS, identity platforms, laptops, APIs, contractors, hybrid networks… and attackers have adapted faster than the tools meant to detect them. These attackers operate in sequences, and sequences reveal intent long before an alert ever fires, yet the SOC still treats intrusions as isolated events.
Your SOC May Not be Looking at the Right Things
Every real intrusion follows a familiar progression:
- A normal-looking login.
- A suspicious-but-allowed PowerShell.
- A scheduled task that blends in.
- A beacon hidden in HTTPS.
- An identity reused in a place it shouldn’t be.
- Lateral movement disguised as “business as usual.”
Individually, none of these steps screams “incident,” but together, they tell the whole story. We’ve always known this, but the problem is scale. No analyst, even your best one, can track these relationships across thousands of identities, assets, logs, and historical breadcrumbs. Not anymore. Not at cloud scale. Not at SaaS velocity. And yet most SOC tooling still expects analysts to manually connect the dots. This is now a modeling problem.
Context Is the New Detection Surface
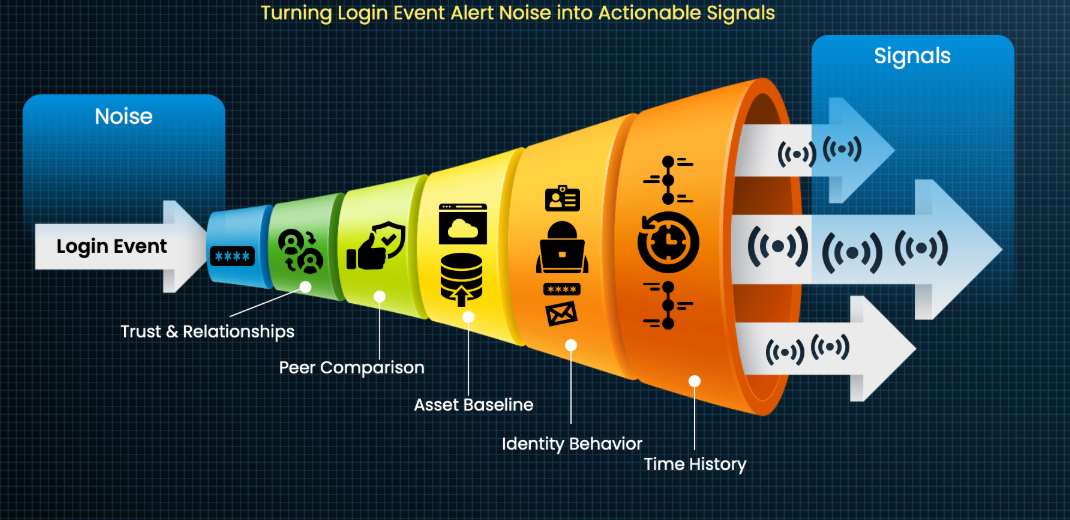
We’ve built the last 20 years of SOC workflows around IOCs: IPs, hashes, domains, URLs.
They still matter, of course, but they never get you ahead of anything because the real signals attackers rely on aren’t found in single events:
- Beaconing only stands out when you see the pattern over time.
- Credential misuse only matters when tied to identity behavior.
- Lateral movement only makes sense when you understand trust relationships.
- DNS misuse only stands out when compared to what’s normal for that system.
The problem is that SOCs are still assembling these fundamentals manually. Attackers exploit the gaps in between tools, not the tools themselves.
Why Models Like the Kill Chain and Diamond Model Still Matter, But Humans Can’t Maintain Them Anymore
Whether you prefer the Kill Chain, the Diamond Model, or ATT&CK, these frameworks all exist to explain how intrusions actually work. The Kill Chain breaks attacks into sequential stages. The Diamond Model describes the relationships between adversary, capability, infrastructure, and victim. ATT&CK catalogs the real techniques attackers use as they move through environments over time.
The point is the same, as intrusions are systems of relationships. Every attacker action implies:
- a capability
- an intent
- a piece of infrastructure
- and a victim that made sense at that moment
Threat hunters intuitively map those relationships in their heads, but modern environments are too big, dynamic, federated, and identity-driven. A human can keep 20 relationships in their brain, but an intrusion might involve 2,000. Attackers aren’t attacking a gap in tooling; they're going after the gap in cognitive bandwidth.
What the Future SOC Actually Looks Like
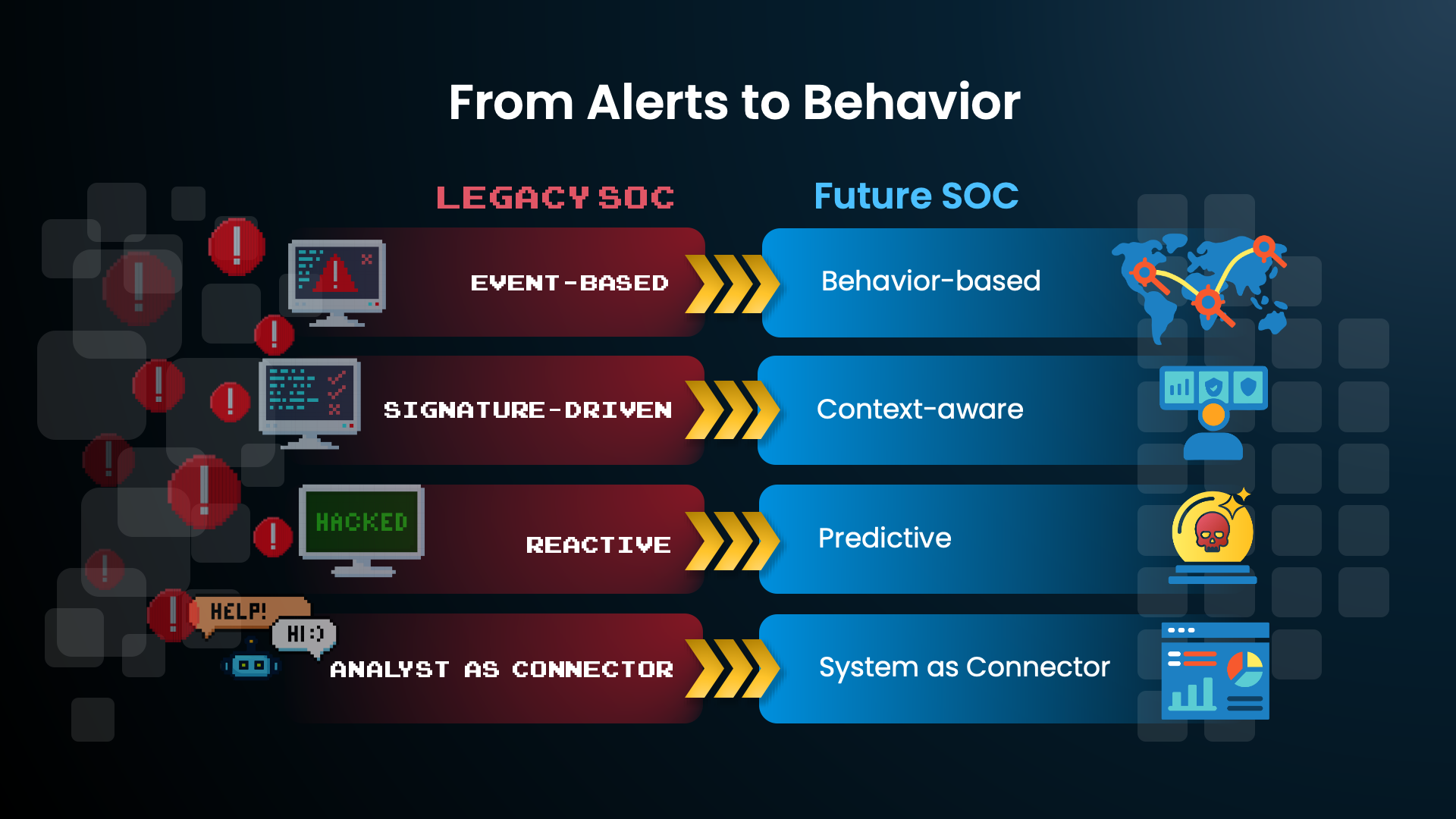
If the old SOC observes events, the future SOC understands the environment. That shift sounds subtle, but it changes everything:
1. Behavior becomes the primary detection signal
Not “did this rule fire?” But “is this normal for this identity, this system, and this moment in time?”
2. Time becomes a first-class citizen
Persistence, beaconing, and delayed actions aren’t catchable in traditional tooling without manual reprocessing. AI can track temporal patterns continuously.
3. Identity becomes the center of gravity
Every attack now pivots through identity. If you don’t model identity behavior and trust boundaries, you’re blind to 70 percent of the real attack surface.
4. ATT&CK becomes executable, not referential
Instead of mapping coverage after the fact, the system asks: “Where would this technique show up here, and would we see it?”
5. The SOC finally stops drowning in alerts
Not because alerts go away, but because alerts are no longer the starting point. The SOC moves from reactive triage to proactive understanding.
The Real Outcome: Time Compression
The value of an AI-native SOC isn’t “better detection, it’s less time.
- Less time to identify compromise.
- Less time to understand what’s actually happening.
- Less time to respond with the right action instead of the loudest one.
When the SOC understands behavior, context, and intent, you shape the battlefield.
Threat hunting hasn’t changed in decades. The only thing that’s changed is the environment, and that environment has outgrown the human brain.
The future belongs to SOCs that stop trying to piece together fragments and start modeling the environment the way real attackers see it: as a connected, evolving system where behavior reveals intent long before alerts do.
Tomorrow’s SOC doesn’t ask analysts to connect the dots. It connects them and shows you the entire picture.


